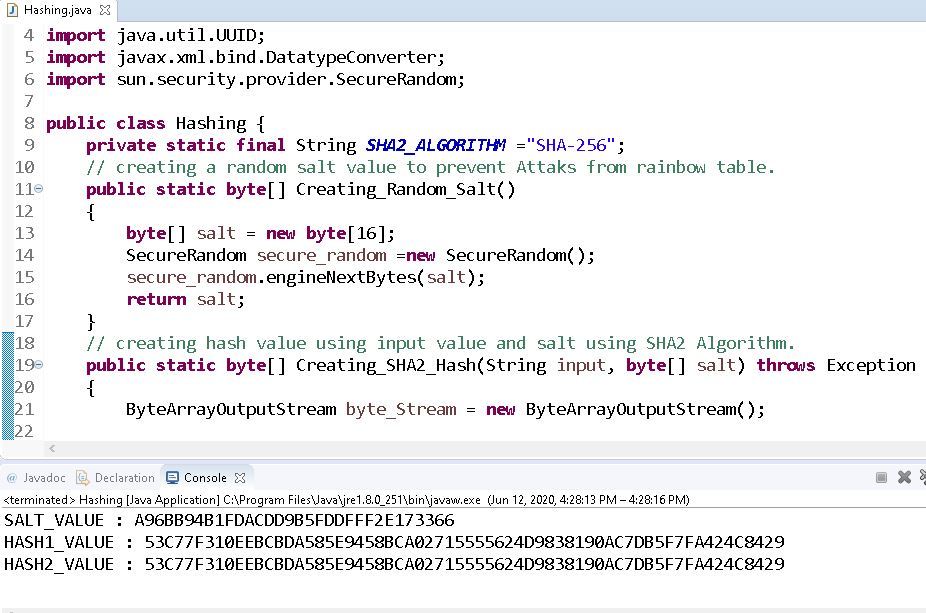
Identifying and Cracking Hashes. During a penetration test or a simple… | by Mr. Robot | InfoSec Adventures | Medium
Analysis Online Reverse Hash Tool v3.3.rar (MD5: C265CCB5D4292C3C3FB91B423270801F) Malicious activity - Interactive analysis ANY.RUN
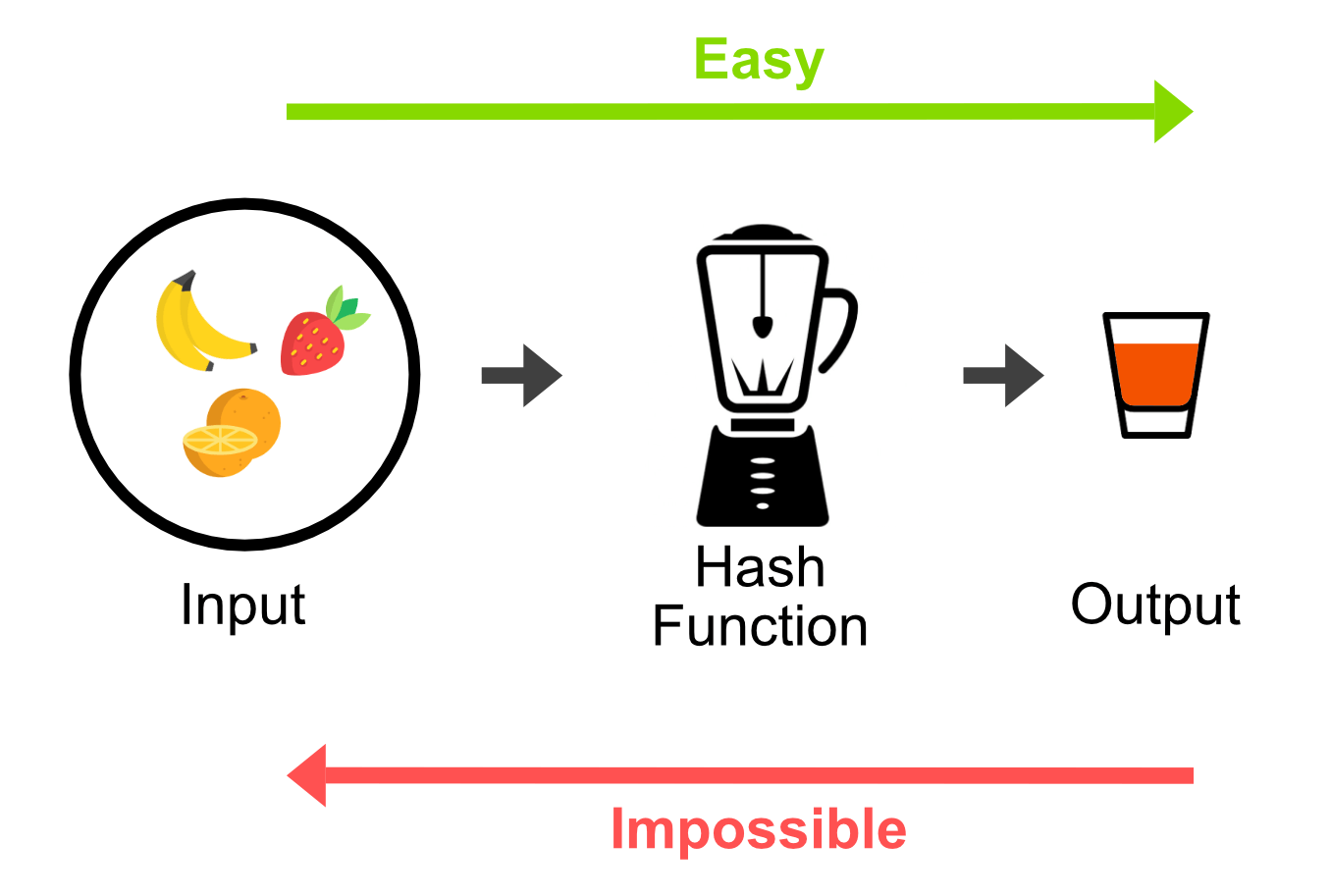
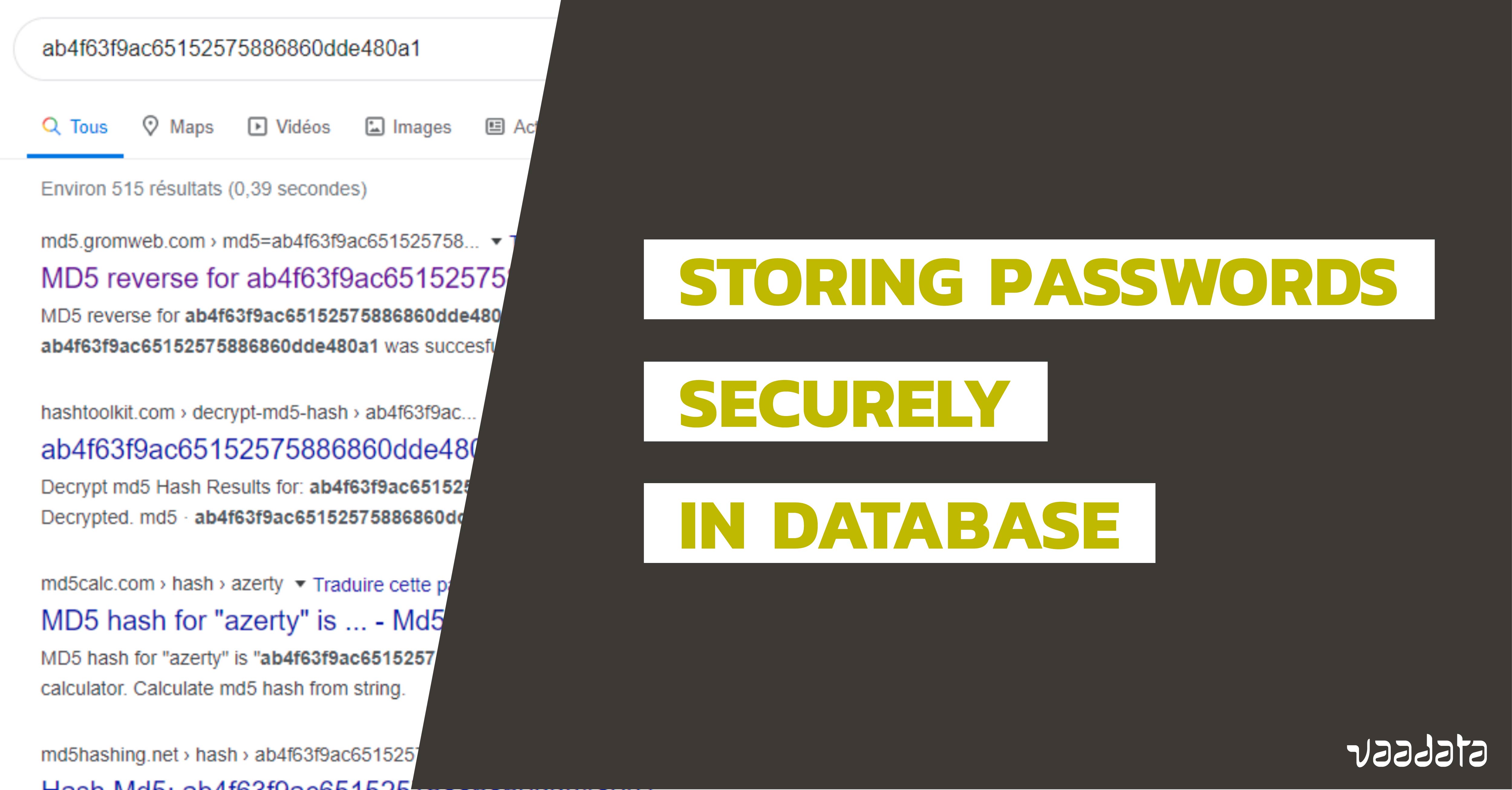
Avoid "dehashing", "reversing", and "decrypting" when talking about password hashes (SHA1, MD5, SHA256, bcrypt, etc.)
Malware analysis Online Reverse Hash Tool v3.3.rar No threats detected | ANY.RUN - Malware Sandbox Online

Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'Online Reverse Hash Tool v3.3.exe'





:max_bytes(150000):strip_icc()/miracle-salad-md5-hash-generator-a6390b6d6fc3473bbd76526eb796975d.png)