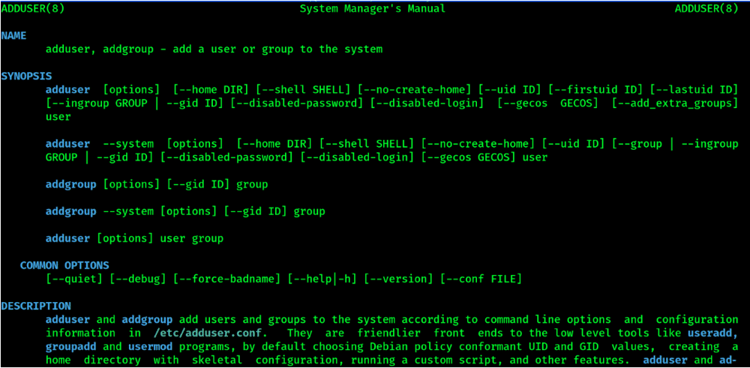
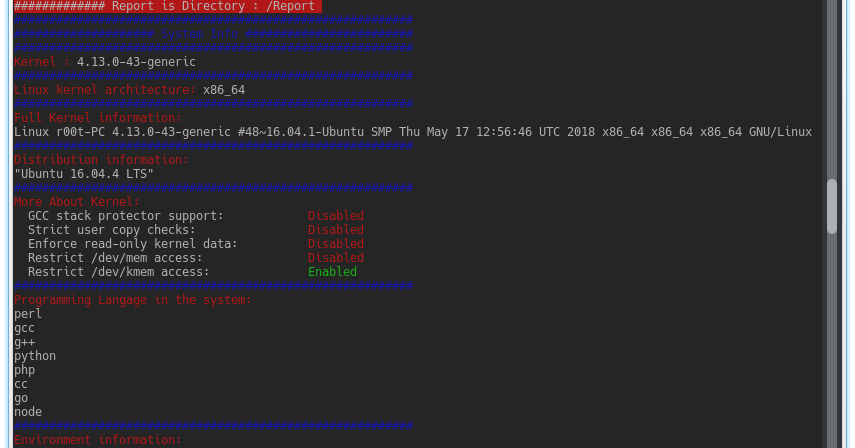
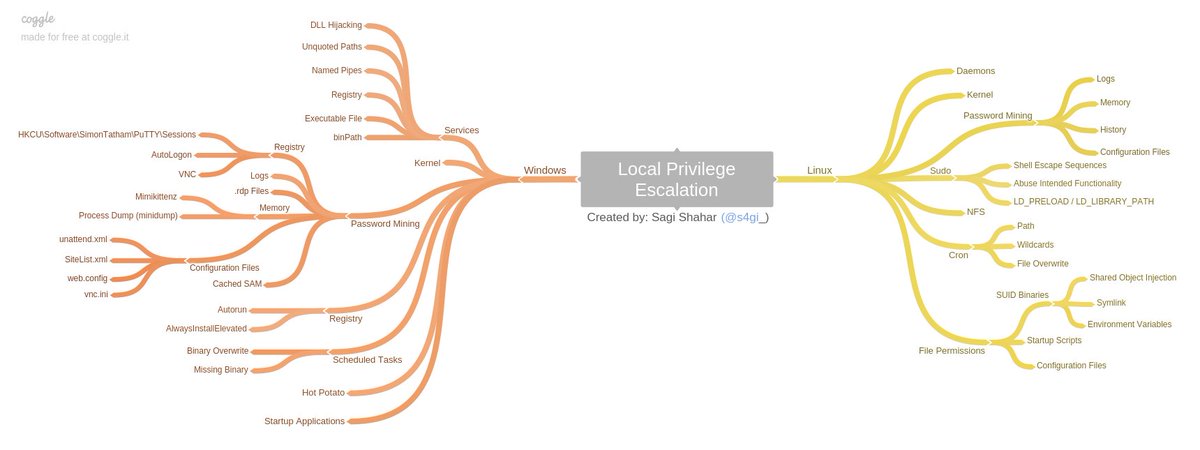
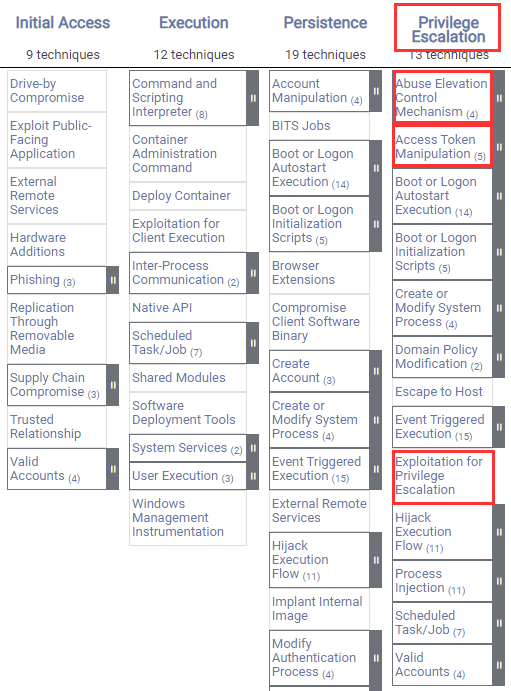
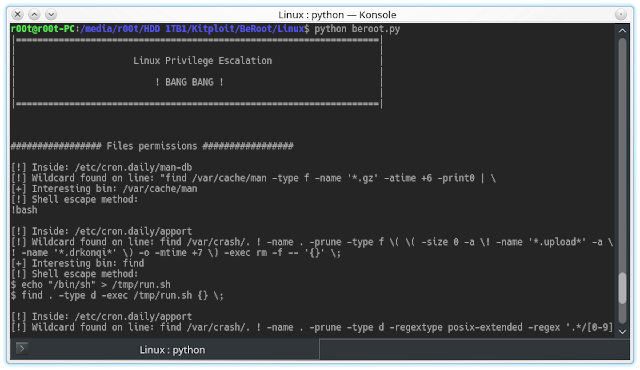
TryHackMe — Jr Penetration Tester | Privilege Escalation | Linux Privesc | Part 2 | by Aditya Sharma | Medium

What Is A Privilege Escalation Attack? How To Prevent Privilege Escalation Attacks? - The Sec Master

Hacking Articles on X: "Linux privilege Escalation Credit @xtremepentest #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness ...

Hacking Articles on X: "Privilege Escalation Tools #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips ...

THE CYBER GUY on Instagram: "Linux privilege escalation is the process of exploiting a vulnerability in a Linux system to gain access to privileges that are not normally available to a user.






![Privilege Escalation with PowerShell Empire and SETOOLKIT [Kali Linux] - Yeah Hub Privilege Escalation with PowerShell Empire and SETOOLKIT [Kali Linux] - Yeah Hub](https://www.yeahhub.com/wp-content/uploads/2018/08/powershell-empire-priv-esc-setoolkit-2.png)