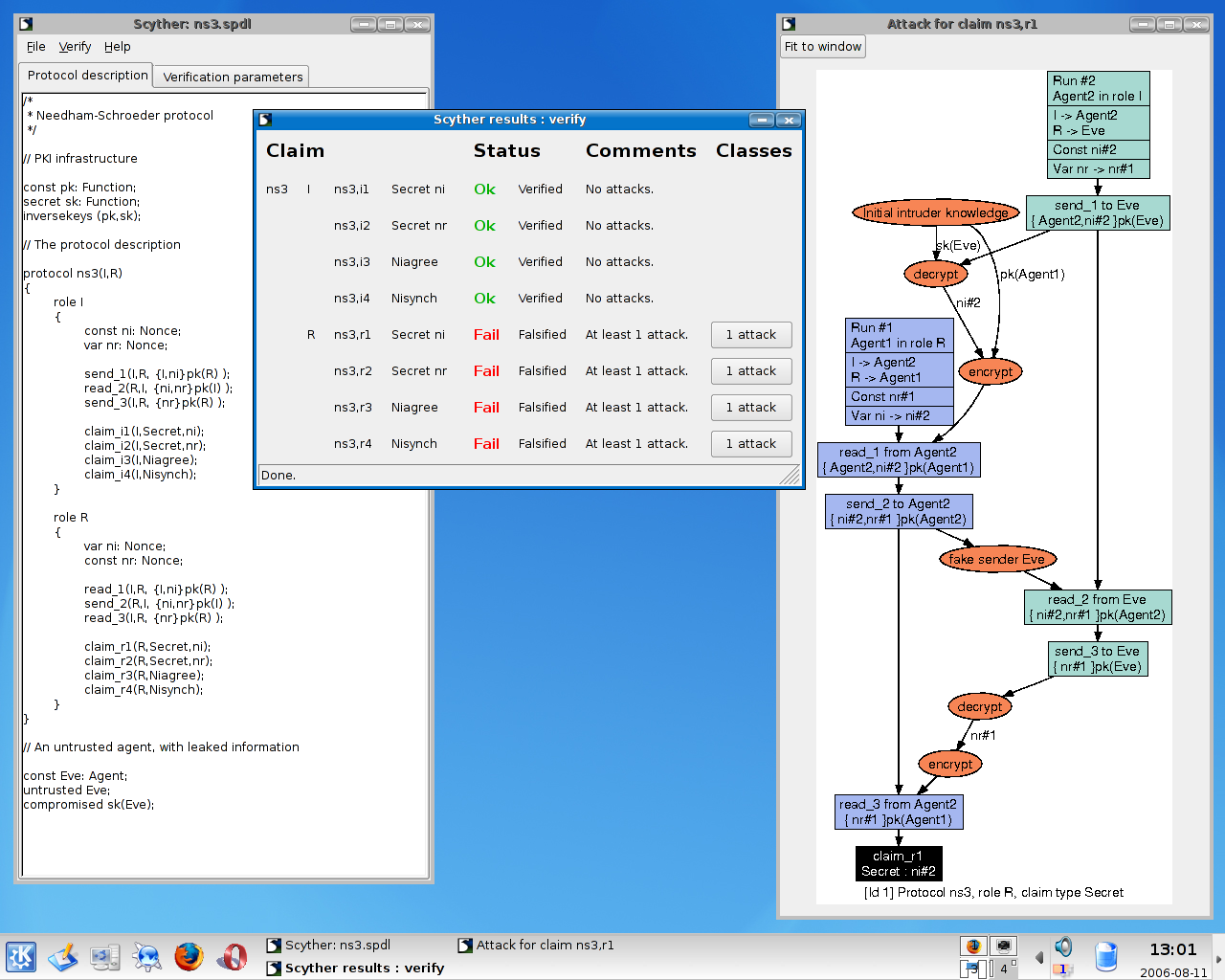
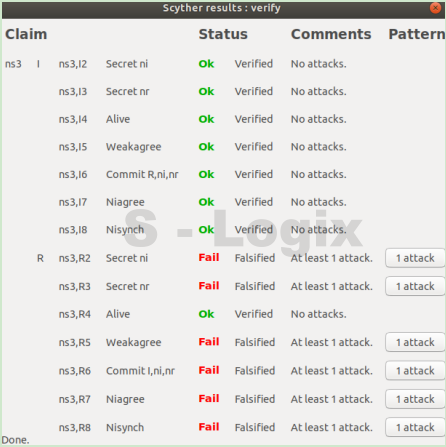
GitHub - binhnguyen1984/scyther-abstraction: The Scyther-abstraction Tool for the symbolic analysis of security protocols

A lightweight three factor authentication framework for IoT based critical applications - ScienceDirect
A Strong Mutual Authentication Protocol for Securing Wearable Smart Textile Applications. - Document - Gale Academic OneFile

An efficient authentication and key agreement protocol for IoT-enabled devices in distributed cloud computing architecture | EURASIP Journal on Wireless Communications and Networking | Full Text